By Ionut Ilascu
Full contact information of everyone attending the BlackHat security conference this year has been exposed in clear text, a researcher has found. The data trove includes name, email, company, and phone number.
The BlackHat 2018 conference badge came embedded with a near-field communication (NFC) tag that stored the contact details of the participant, for identification or for vendors to scan for marketing purposes.
In a different record of the chip, the reader pointed the user to the BCard app – a business card reader for Android and iOS.
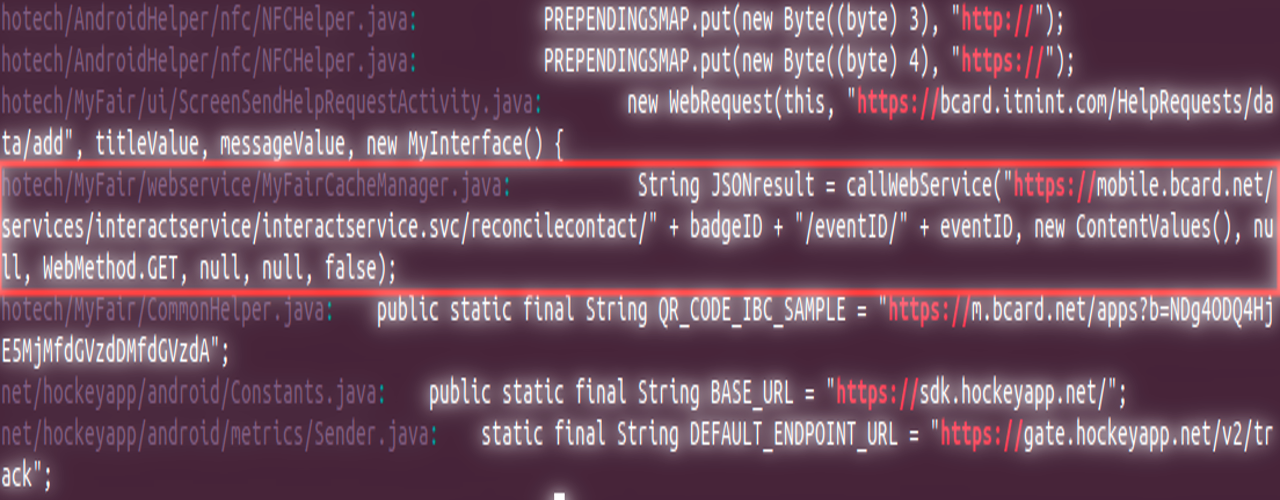
NinjaStyle started prodding the recommended card reader and decompiled its APK in search for potential API endpoints. He found out that BCard created a custom URL using the badge and event identification values of the badge owner, and he determined how the values were built.
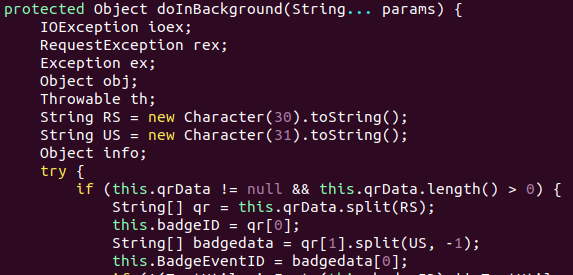
“Though we can prove this in the code shown above, I simply guessed that those values corresponded to the eventID and badgeID parameters by sending the request in Firefox. To my surprise, I was able to pull my attendee data completely unauthenticated over this API,” writes NinjaStyle in a blog post disclosing the glitc
“With an estimated 18,000 BlackHat attendees, we can then assume that we will enumerate a valid badgeID in approximately 2% of our requests,” he concluded.
Using Burp Suite to test his theory, NinjaStyle estimated that getting the contacts of all BlackHat participants would take about six hours; it’s a very decent waiting time, considering that in the security industry the conference is the main event for hackers, corporations and government agencies around the world.
A troublesome API is not an isolated thing, even if it serves the audience of a security conference. The official app for the RSA Conference this year ran unprotected and allowed participant information to be leaked. In total, 144 records were accessed without authorization.


